 The software security measures that have been developed for directory and file permissions on computers and servers connected to the global network may incredibly reveal one of the main applications in which the number 666 will be used in the economy of the Beast. In fact, it is already being used even before the Antichrist and the Mark arrive. The security setting sometimes referred to as chmod 666 (chmod means change mode) is a UNIX permissions setting that designates the level of access allowed to protected folders and files. Derivatives of UNIX (particularly Linux but also the Mac OS X) are the most commonly used operating systems on servers that run the Internet and the World Wide Web today. Permission settings are used as part of the server security measures to allow only authorized users to access certain locations in file system hierarchies, especially when connected to the Internet through computers or point of sale (POS) terminals. When accessing commercial web sites or when using POS terminals in retail stores, the servers that control the processes behind the scenes contain important data to support the web experience and also provide security for electronic buying and selling of goods and services. Using the correct security settings will permit access to only those files and information intended to be accessed and nothing else. As we will see in this section, the security permissions setting 666 will soon be used alongside the Mark of the Beast and the 666-containing EAN/UPC barcode technology to allow a person to participate in electronic buying and selling in a cashless society, precisely as predicted in Revelation 13:18.
The software security measures that have been developed for directory and file permissions on computers and servers connected to the global network may incredibly reveal one of the main applications in which the number 666 will be used in the economy of the Beast. In fact, it is already being used even before the Antichrist and the Mark arrive. The security setting sometimes referred to as chmod 666 (chmod means change mode) is a UNIX permissions setting that designates the level of access allowed to protected folders and files. Derivatives of UNIX (particularly Linux but also the Mac OS X) are the most commonly used operating systems on servers that run the Internet and the World Wide Web today. Permission settings are used as part of the server security measures to allow only authorized users to access certain locations in file system hierarchies, especially when connected to the Internet through computers or point of sale (POS) terminals. When accessing commercial web sites or when using POS terminals in retail stores, the servers that control the processes behind the scenes contain important data to support the web experience and also provide security for electronic buying and selling of goods and services. Using the correct security settings will permit access to only those files and information intended to be accessed and nothing else. As we will see in this section, the security permissions setting 666 will soon be used alongside the Mark of the Beast and the 666-containing EAN/UPC barcode technology to allow a person to participate in electronic buying and selling in a cashless society, precisely as predicted in Revelation 13:18.
As the world moves closer to an economy designed around the Mark of the Beast several critical technologies are being developed and merged together to allow the final system to operate. As we have seen in previous sections on the topic of the Mark, this includes the advent of computer technology; the elimination of cash through the use of credit cards, debit cards, and smart cards; the development of the global electronic network which forms the basis for the Internet, the World Wide Web, and electronic funds transfer (EFT); and the advent of biometrics to eliminate fraud by positively confirming identities. In all of these inventions and developments, security has become the principal requirement and driving force for the creation of a cashless society that allows people to make purchases electronically without the physical exchange of money and also while preventing fraud. The security permissions setting 666 has become a vital part in this system.
The development of the Internet and the Web also required important security considerations to be designed into the software to protect the files and information on the servers that contain data used to create web pages. This data might contain information that gets displayed when a site is visited or it might contain the personal confidential information of members or people who have accounts with a company. People who visit web sites want to view the pages and information that the sites have available; however, the owners of the web sites don’t want people to be able to access the raw databases and programs that support their sites on the hosting servers. They also want to prevent visitors from accessing the account information of people who have registered with their site or have done business with them in the past. Financial information, tax documents, social security numbers, account numbers, names, addresses, and other private information must be maintained in complete security for the system to work with confidence. For this reason, the operating systems that control the servers all have security levels that can be set for directory (folder) and file access. Web sites use data and executable programs on their servers to create and present finished web pages to visitors, but their security systems also prevent anyone from actually accessing or changing the data and programs so that no malicious activity can occur. Unless the system allows for specific access to particular directories or files on a web server, a visitor cannot see them merely by visiting a web site or entering an Internet address, even if that Internet address happens to refer to an actual folder or file on the server. With the proper security in place, any attempt to access a restricted part of a server without the appropriate permissions will result in an error message or a “page not found” response. As we will see, this is where the security permissions setting 666 comes into play.
The majority of Internet servers now run a version of Linux as their operating system, which is an open source derivative of UNIX. The Linux family uses the same permissions settings originally developed for UNIX systems decades ago. The permissions can be set on an individual directory (folder) or at the file level using either a set of letters or numbers representing the type of security desired. Three different types of users are recognized within Linux permission settings and each type can be given different levels of security access for folders or files. The three types of potential users are: (1) the owner of the file or directory (i.e., the administrator or controller of the folder or file), (2) the group that is associated with the directory or file (for instance, an accounting group within a company’s network or members registered on a web site), and (3) all other users (often simply called “others”).
In addition, four levels of security are available for each of these different types of users when providing directory or file access and the last three of these levels can be combined in any way. The four options for security access to users are: (1) no access, (2) read-only access, (3) write access (which includes modifying or deleting files), and (4) execute access (or the ability to run programs or search within folders). UNIX and Linux systems assign letters and numbers that are associated with each of these security settings according to the following table:
| Security Setting | Letter Code | Number Code |
| No access | – | 0 |
| Read-only | r | 4 |
| Write | w | 2 |
| Execute | x | 1 |
As the diagram shows, there also is another set of indicators before the permission settings that refers to whether the location is a directory (d) or simply a file (-). These occur before the security settings to let the operating system know whether they apply to an entire folder with all its contents or to just an individual file within a folder. If we consider the various types of users and the possible levels of security that can be defined for each one, we can illustrate any possible permissions setting using this diagram as a guide. In the convention of UNIX or Linux operating systems, the list of permission settings for each type of user is presented as a linear sequence of letters. Therefore, if the owner, group, and other users all are given equal access as well as the highe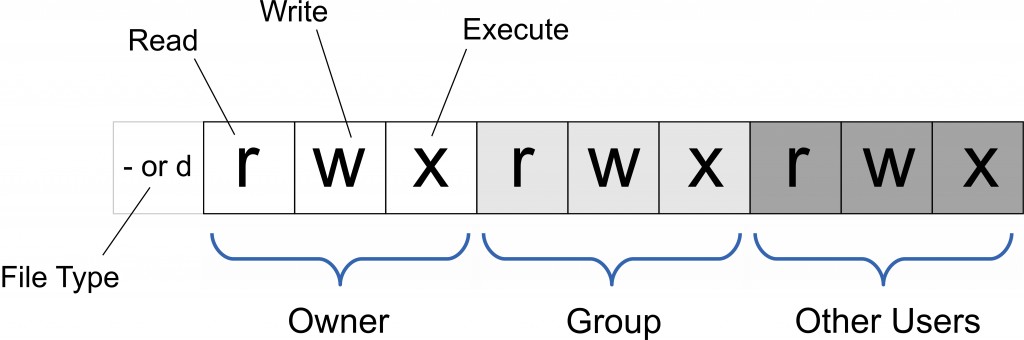 st (total) access credentials the permissions would be indicated by:
st (total) access credentials the permissions would be indicated by:
rwxrwxrwx
This highest level security setting indicates read (r), write (w), and execute (x) rights for each type of user. The first three letters correspond to the settings for the owner or administrator of the file or folder, the middle three letters indicate the settings for the group level users, and the last three letters are the security settings for all other users. Using this format, if the owner wanted to be the only one designated with total access but wanted to prevent other types of users from executing programs, then the security settings might become:
rwxrw-rw-.
In this case, both the group and other users categories have only read and write access capability, but no execute permissions (indicated by the dashes in the execute position). Similarly, the administrator could deny anyone else from access to a file or directory by using the following settings:
rwx——
This setting indicates that the group and other users have no access rights to the file or directory at all (three dashes for groups and three dashes for other users). As can be seen, these security settings in UNIX or Linux (and also present in the Mac OS X operating system) are very powerful and allow an administrator to set unique permissions for every folder or file on a server (or on any computer for that matter running one of these operating systems). Now, how does all of this relate to the security permissions setting 666? We have to learn one additional aspect of these security settings to find out.
Another way of looking at permissions settings is to use the corresponding number code for each security level. This is where it gets very interesting for students of end times prophecy. According to the previous table, a security setting of no access is equal to the number 0; a setting of read-only access equals 4; a setting of write access is equal to 2; and a setting to allow execution of programs equals 1. In UNIX or Linux, these number values are additive for each type of user, and the end result of adding these number values together represents a quick way to summarize the security levels for any file or folder. Thus, for a security setting where every type of user has all possible access rights (rwxrwxrwx), the corresponding number designation would be calculated as seen in the neighboring illustration.
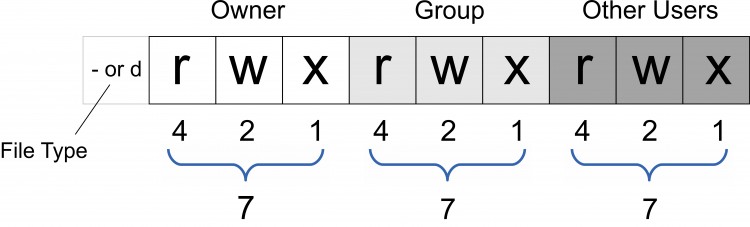 Since the owner of the file or folder is given the complete permissions of read, write, and execute, the number value for this setting is calculated by adding the numerical values of each permission setting, or r+w+x = 4+2+1 = 7. In the same manner, the permissions settings for the group and other users categories are also added together to give a final permissions setting of 777 for the given file or folder. The designation of 777 is sometimes called “God-mode”, since it allows total access and control over a file or directory by anyone. It is curious that the number 7 is often associated with God in the Bible, too. As you can imagine, however, it is not likely that any directory or file on an Internet server would ever be given the 777 permissions setting, because that would result in any visitor to the web site being able to do whatever they want with it, including accessing confidential information, changing the site, or even deleting it from the server.
Since the owner of the file or folder is given the complete permissions of read, write, and execute, the number value for this setting is calculated by adding the numerical values of each permission setting, or r+w+x = 4+2+1 = 7. In the same manner, the permissions settings for the group and other users categories are also added together to give a final permissions setting of 777 for the given file or folder. The designation of 777 is sometimes called “God-mode”, since it allows total access and control over a file or directory by anyone. It is curious that the number 7 is often associated with God in the Bible, too. As you can imagine, however, it is not likely that any directory or file on an Internet server would ever be given the 777 permissions setting, because that would result in any visitor to the web site being able to do whatever they want with it, including accessing confidential information, changing the site, or even deleting it from the server.
To make the Internet work properly and maintain security against malicious activity, most files and folders are restricted in their access except to a valid owner or administrator of the site, who would be given a higher level of control (at the 7 level) only through the secure access to a special administrator page. Most of the time, when a web site is just visited from an external computer the permissions for all users would be restricted to the read-only level, which is especially suited for the browsing and reading of web pages. Therefore, an appropriate security setting for a web server would be 444, which indicates that every type of user has only read capabilities, but not write or execute permissions. This allows visitors to browse the web pages and access information, but not make changes to the site itself. Only a valid administrator of the web site could gain a greater permission level through signing into a special admin control panel using a password.
However, many Internet sites allow users to fill out forms, post comments, register to become members, or make purchases and transfer money. Under these circumstances the permissions settings for certain files or folders must be temporarily set higher than read-only and are typically set at the read and write level. In fact, the default level for the creation of a new file in UNIX or Linux is at the read and write permissions setting for all users, because otherwise the file could not be created and saved on the server. Therefore, in order to use the Internet for interactive services or for buying and selling, the initial permissions settings must be at the read and write level for all users. If this were not the case, then no records of the users’ interactions could take place. If a web site visitor was making a purchase, for instance, the server would have to maintain a record of what was purchased and the prices associated with the purchase. The only way to do this would be to have read and write capability within a file or folder associated with the user so that a permanent record could be created. The web page on which the transaction takes place also must have read and write capabilities to allow a user to document the items purchased, enter details on their personal identity, and perform payment transfers with some form of currency. During online purchases or when using cards at POS terminals, one or more servers somewhere in the electronic global network must be able to accept the purchase and make a record of it. In addition, the issuing card company or bank has to make a record of the purchase information in the background. All of these activities run behind the scenes during an Internet purchase session and are typically transparent to the customer. Thus, for the Internet to function as it does today, when any of these interactive or commercial activities take place the operating system permissions have to be set at the read and write level for the appropriate folders or files. This is where the security permissions setting 666 comes into play.
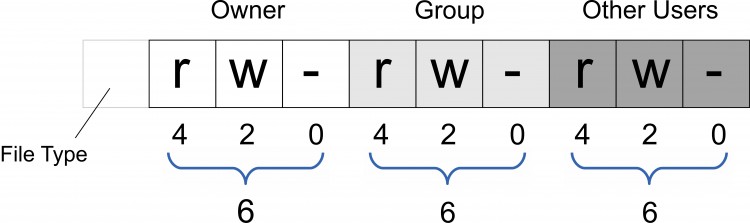 Therefore, for buying and selling in a cashless society the operating protocols are associated with permission settings for owners, groups, and other users at the read/write level, or “rw-rw-rw-” in the syntax of UNIX or Linux. And what does “rw-rw-rw-” correspond to in the numbering system of UNIX permissions? In the shorthand numerical format of presenting permission settings, the designation “rw-rw-rw-” also can be numerically added together as 4+2+0, 4+2+0, 4+2+0, which equals a security setting of 666!
Therefore, for buying and selling in a cashless society the operating protocols are associated with permission settings for owners, groups, and other users at the read/write level, or “rw-rw-rw-” in the syntax of UNIX or Linux. And what does “rw-rw-rw-” correspond to in the numbering system of UNIX permissions? In the shorthand numerical format of presenting permission settings, the designation “rw-rw-rw-” also can be numerically added together as 4+2+0, 4+2+0, 4+2+0, which equals a security setting of 666!
This is incredible! Even before the Antichrist arises, the Empire-Beast has developed the electronic network and protocols necessary to allow the Mark of the Beast to function in a cashless system. Yes, the Number of the Beast or 666 is now being associated with every commercial activity done over the Internet, the World Wide Web, or through EFT networks today. It is also associated with every interactive activity, such as leaving comments on web sites or filling out registration forms or surveys. However, the most important aspect related to Biblical prophecy is how the security permissions setting 666 is being used to allow buying and selling in an electronic world. As the Empire-Beast moves forward toward a cashless society where money substitutes such as smart cards and validated identities will replace the exchange of physical currency, the security permissions setting 666 will make all of these transactions possible!
How close to you think we are to the Return of Christ seeing that all of these things are taking place in our world today?
Note: A minor percentage of the Internet server systems currently are run using the Windows Server operating system, which uses a security system with similar capabilities, but it does not have the 666 designation as part of it. The prophecy of the Number of the Beast may indicate that the final system will standardize on the Linux operating system to make the Antichrist’s economy function at the end.


